 mybucks.online
mybucks.online
 mybucks.online
mybucks.online
Your money is online, and it's safe
Be the sole owner of your crypto.
Just a password - no seed phrases to remember.
No tracking, no email, no ID. Just for you.

A wallet address is generated from your password and passcode.
This process is one-way and irreversible, verified by industry standards.
And nobody knows your credentials, nobody stores them.
Learn moreSay goodbye to seed phrases. Forget about cumbersome registration processes, emails, 2FA, and KYC.
Secure your crypto assets with a password and passcode only. No footprint, keep everything in your mind.
Access my wallet
The Scrypt and Keccak256 hash functions turn your credentials into a private key. The Scrypt KDF(Key Derivation Function) requires significant memory to compute, making brute-force attacks computationally expensive and impractical.
It fully runs on your browser side and does not transfer your password to other parties.
This method ensures a non-custodial, admin-free, installation-free, setup-free solution with no storage required anywhere.
Learn more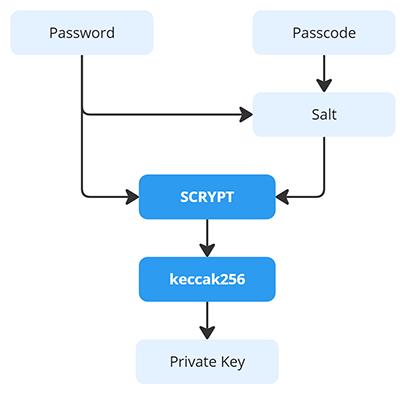
SCRYPT:
N: 32768
r: 8
p: 5
keyLen: 64
Create a random wallet, deposit cryptocurrency into it, and share the wallet with your friends by providing the password and passcode, or even as a URL.
This makes gifting and airdropping very easy.
Try this demoSecure3 is a battlefield where elite auditors compete to safeguard Web3 innovations against security threats.
They have provided security audits for over 140 projects, including zkSync, Polkadot, and more!
View reportMybucks.online turns your credentials into wallet private key directly, without the need for seed phrases, site registration, 2FA, or KYC. Only the password and passcode determine the private key and wallet address, making it extremely convenient to use for sending and receiving blockchain assets. This uses the Scrypt KDF(Key Derivation Function) and Keccak256, and this makes brute-force attacks computationally expensive and impractical compared to old-school "Brain wallets".
Using a computation-intensive hash function makes brute-force attacks impractical. The Scrypt and Keccak256 hash functions produce pseudo-random values and are widely verified and accepted across the industry. And there is no storage, no backend for your credentials. It does not require any personal information and sharing the wallet address does not compromise the private key or password.
By utilizing a password as a key, it eliminates the need for seed phrases, site registration, or separate private key storage, ensuring user-friendliness without compromising safety. It is self-custodial, decentralized, hosted on a public domain and instant-access. No KYC is required, and truly self-custodial.
With MyBucks.online, you can "Send the Wallet" instead of just the coins by sharing a simple URL via Telegram or WhatsApp. The recipient just clicks the link to instantly take full ownership of the assets with no app installs or registration required. This makes it perfect for gifting and airdropping.
You can use this wallet to securely store, transfer and receive cryptocurrency. It is ideal for both Micro-transactions and gifting. However, it is not intended for interaction with Web3/dApps.
The wallet itself is free to use, but standard blockchain transaction fees will apply. Your generous donations help us continuously enhance and improve our product.
You can't reset or recover the password and passcode. Do not forget it, and back it up. And there is no direct method to change the password and passcode. Each password and passcode generates a unique wallet.
Currently, it supports 8 EVM compliant networks including Mainnet, BSC, Polygon, Avalanche, Arbitrum, Optimism, Base and TRON. Adding Solana and the TON network is planned.